Cloud
Enterprises face unique challenges as they move their core IT into the cloud. Your complex IT environment creates the need for flexibility and customization that few cloud providers are able to offer. The scale of your existing infrastructure makes migration fraught with risk. And you are putting compliance in the hands of another party. Cloud deployments require more than an IT strategic plan to effectively develop a robust cloud and Data Center infrastructure solution given the complexity and range of products available in the market today. Also, hiring, training and retaining talented cloud and Data Center experts are industry wide challenges faced by every organization.
Network Infrastructure
Network Infrastructure deployments require more than an IT strategic plan to effectively develop a robust LAN, WAN and Data Center infrastructure solutions given the complexity and range of products available in the market today. Also, hiring, training and retaining talented Network and Data Center experts are industry wide challenges..
Application and Desktop Virtualization
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
Contact Center
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
Ultra Low Latency
In the financial vertical, time is money and both latency (measured at very low nanosecond speeds) and the guarantee of deterministic latency characteristics is critical to the success of Hedge Funds, Multi Asset Trading Environments, and Quantitative algorithmic environments for both the financial community and the scientific research community….
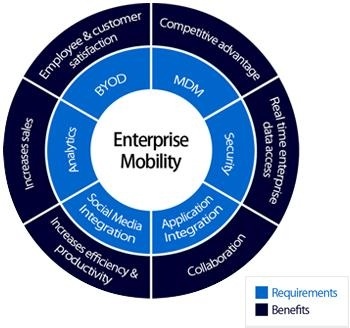
Enterprise Mobility
To some, “wireless” equates to Wi-Fi enabled laptops, but it’s much more than that – the world today relies on mobile and smart phones, iPhones, BlackBerry devices, PDAs, and two-way radios to communicate. Your employees, customers, clients, students, patients or guests need ALL these wireless tools to work – especially indoors!…
Infrastructure Security
When infrastructure solutions age, often they end up performing in a less than optimal way. The same is true for security appliances: as they age, typically devices will get over/under configured and can lead to unexpected threats, vulnerability and performance issues. Additionally, changes to the organizations…
When infrastructure solutions age, often they end up performing in a less than optimal way. The same is true for security appliances: as they age, typically devices will get over/under configured and can lead to unexpected threats, vulnerability and performance issues. Additionally, changes to the organizations, security posture can affect the quality of a solution across its lifecycle.
Managed Security
Threats are growing more hostile. Budgets are tight. Skills are at a premium and business imperatives like mobility, social media, web applications and big data can pose risks as well as inefficiencies if they’re not properly managed. Information security services span your network, endpoints, vulnerability management, monitoring and analysis. We extend your security operations to bridge people, processes and technology for 24x7 support.
Infrastructure Security
When infrastructure solutions age, often they end up performing in a less than optimal way. The same is true for security appliances: as they age, typically devices will get over/under configured and can lead to unexpected threats, vulnerability and performance issues. Additionally, changes to the organizations…
When infrastructure solutions age, often they end up performing in a less than optimal way. The same is true for security appliances: as they age, typically devices will get over/under configured and can lead to unexpected threats, vulnerability and performance issues. Additionally, changes to the organizations, security posture can affect the quality of a solution across its lifecycle.
Let's Start Something new
Hitorra America is ready to help your organization secure, modernize, and grow through the use of leading-edge technology solutions. Contact our team to start today!
We're Here To Help!
Office
New York, NY 10017
Hours
S-S: Closed